vSphere 6.5 – Secure Boot (ESXi and VMs)
When new feature Secure Boot is enabled, the UEFI firmware validates the digitally signed kernel of an operating system against the digital certificate stored in the UEF firmware. For ESXi 6.5 this capability is further leveraged by the ESXi kernel, adding cryptographic assurance of ESXi components.
ESXi is already made up of digitally signed packages, called VIB’s. (vSphere Installation Bundle) These packages are never broken open. At boot time the ESXi file system maps to the content of those packages. By leveraging the same digital certificate in the host UEFI firmware used to validate the signed ESXi kernel the kernel will then validate each VIB using the Secure Boot Verifier against the firmware-based certificate, ensuring a cryptographically “clean” boot.
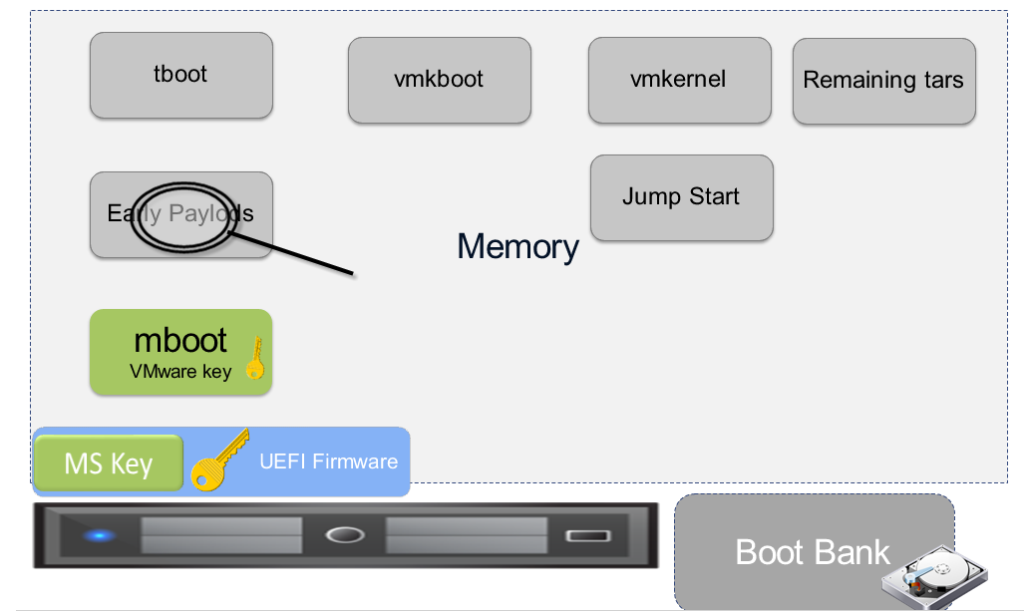
ESXi Secure Boot operations
- Installation of un-signed VIB’s/code will be prevented if SecureBoot is enabled.
- Installation of un-signed VIB’s can only be done if SecureBoot is disabled in the BIOS
- Enabling SecureBoot after un-signed VIB installation will cause a PSOD at boot time
- If you are running unsigned drivers you cannot use SecureBoot
- VIB Certificate Chaining
Virtual Machine Secure Boot
Enabling Virtual Machine Secure Boot is as simple as just checking the box in the UI.
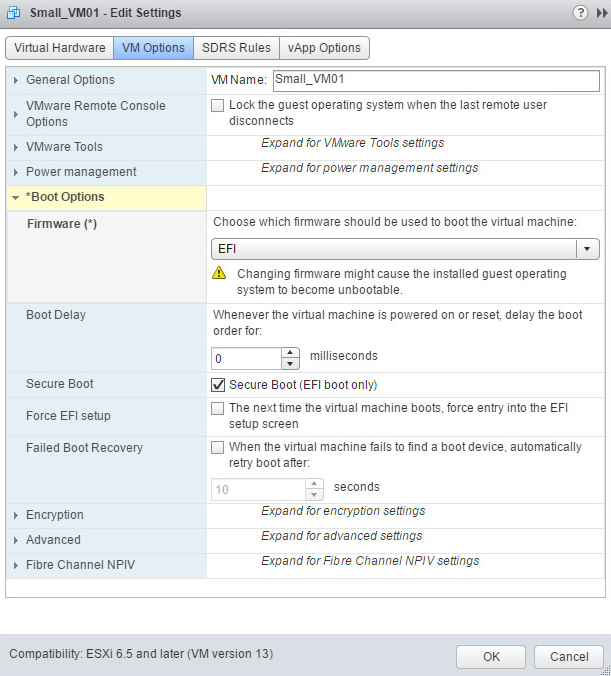
Virtual machines must be boot from the EFI firmware to enable Secure Boot. There is support for Windows, Linux and nested ESXi in the EFI firmware. In order for Secure Boot to work, the Guest OS must also support Secure Boot. Some examples are Windows 8 and Server 2012 and newer, VMware Photon OS, RHEL/Centos 7.0, Ubuntu 14.04 and ESXi 6.5. For virtual machines, enabling Secure Boot requires that the VM is running with “EFI” firmware. Note that you can’t just change the firmware for some OS’s. When using EFI firmware, the Secure Boot checkbox becomes enabled.
2 thoughts on “vSphere 6.5 – Secure Boot (ESXi and VMs)”
Hi – how can you do this via Powercli?
Thanks
Ryan
Hi Rayan,
For sure you can do it with PowerCli – here in the documentation you will find commands explaining how to do it:
https://docs.vmware.com/en/VMware-vSphere/6.5/com.vmware.vsphere.security.doc/GUID-898217D4-689D-4EB5-866C-888353FE241C.html
Comments are closed.