Policy management with Tanzu Mission Control
Management of multiple Kubernetes clusters isn’t an easy task. Especially if we are talking about dozens or hundreds of Kubernetes clusters you need to take care of which is not an unusual situation nowadays.
So how I can manage all of them in a consistent way and at the same time doing it effectively without spending weeks on applying the configuration?
VMware Tanzu Mission Control a.k.a TMC is the answer! It allows us to centrally define and propagate following policy types:
- Access Policies
- Image Registry Policies
- Network Policies
- Security Policies
- Quota Policies
- Custom Policies
- Policy Insights
And just to make it clear here – these policies are not applicable only to VMware Tanzu Kubernetes Grid clusters. Other platforms are supported as well! That means consistency in a truly multi-cloud Kubernetes infrastructure.
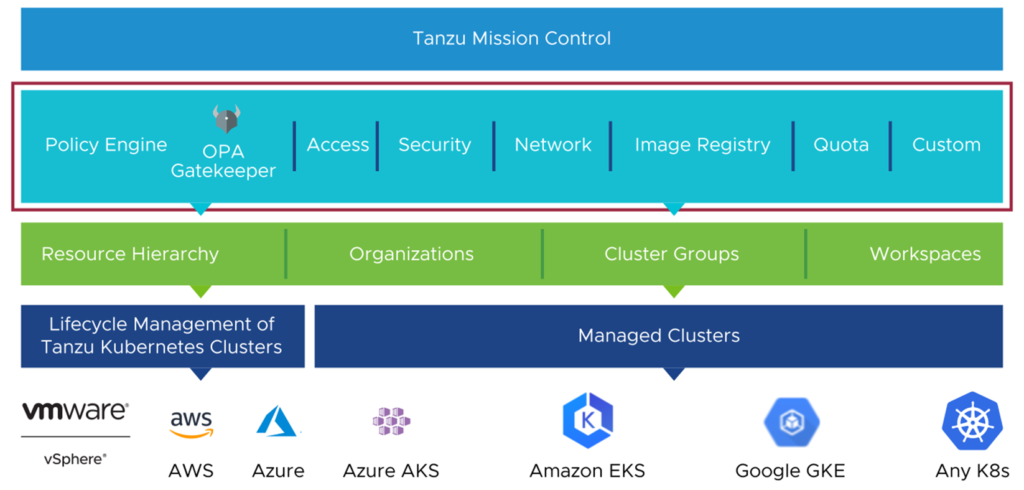
Let’s dig a little bit deeper discussing each of them.
Access policies – provides role-based access control (RBAC) to clusters and namespaces which allows us to control permissions that are granted to the users. These policies are implemented and mapped to Kubernetes resources such as Role, ClusterRoles, RoleBinding, and ClusterRoleBinding.
Image registry policies – provides a capability do control and define images that can be pulled from registry and in general define the registries from which images can be pulled based on variety of patterns. As there is no native Kubernetes resource that would be able to support that use case image registry policies are implemented using OPA Gatekeeper.
Network policies – define how pods communicate with each other and other network endpoints. Probably the most common type of policies we need but also not easy to implement using native Kubernetes resource named NetworkPolicy (which by the way is used to implement network policies defined from TMC). The point that’s worth to mention here is that TMC gives you a kind of graphical UI to define these firewall rules that will be translated to a YAML used to define NetworkPolicy. Therefore you don’t even need to know the YAML structure to get them implemented!
Security policies – allow to define constraints on a Kubernetes cluster that define what pods can do and which resources they can access. One of the commonly used options as part of security policies was to disable native Kubernetes Pod Security Policies (PSP) until they were finally removed in Kubernetes 1.25. Security policies are implemented using OPA Gatekeeper.
Quota policies – could be used to define limits on the resources that can be consumed by namespaces in a cluster. Implemented using native Kubernetes ResourceQuota resources.
Custom policies – probably the most complex due to the requirement of templates written in Rego but quite powerful, though. Can be used to address aspects of cluster management that specifically suit the needs of an organization. For instance to enforce labels and values on Kubernetes resources or envorce the HTTPS only ingress, etc. Implemented using OPA Gatekeeper.
TMC provides a GUI to define all of these policies which not only saves time but also provides a mechanisms to monitor compliance across our clusters whether these policies are enforced and information about any violation attempts.
If you didn’t have a chance to use TMC and policy management – stay tuned, in the next articule I’m going to present how to use each of them in practice!