vSphere 6.5 – VM Encryption
Next new security functionality in vSphere 6.5 – encryption is implemented via Storage Policies. If You add to the vm an encryption storage policy it will encrypt the disk.
Key features:
- No modification within the Guest.
- VM Agnostic
- Guest OS
- DataStore
- HW Version
- Policy driven
- Encrypts both VMDK and VM files
- No access to encryption keys by the Guest
- Full support of vMotion
Diagram below shows how it works:
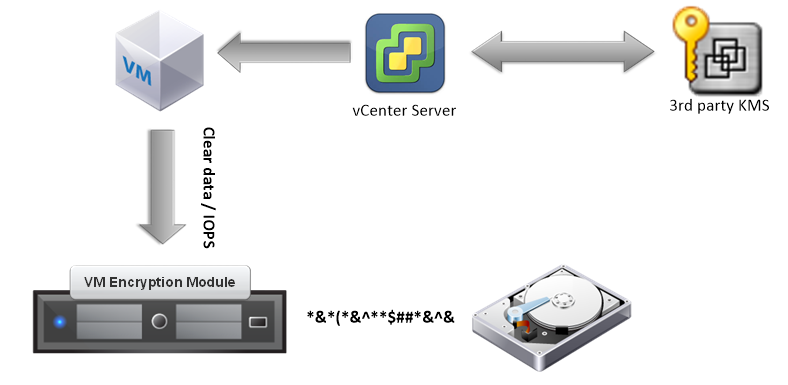
- Register a VM on a host and configure the (new or existing ) VM with Encryption Enabled storage policy and KMIP server
- vCenter gets a key from the KMIP server. That key is used to encrypt the VM files and the VM Disks.
- VC loads the key into the ESXi hosts. All hosts that don’t have the key will get the key to support DRS/HA.
- Once the key is loaded into the KeyCache on the ESXi host, encryption and decryption of the disk will happen at the IO Filter (introduced in 6.0 U1) level.
But let’s ask who can manage vm encryption ?
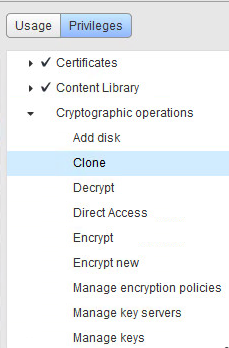
… Security Administrators will manage KMS and keys only “subset” of vSphere Admins will / should manage encryption within vSphere. We have new default role “No Cryptography Administrator” , additional we got new vCenter crypto priviledges like : Encrypt, Decrypt, Manage Keys , Clone. So we basically can delegate encryption priviledges to varius admins via custom roles in the way that we well know from previous environment editions – below example :
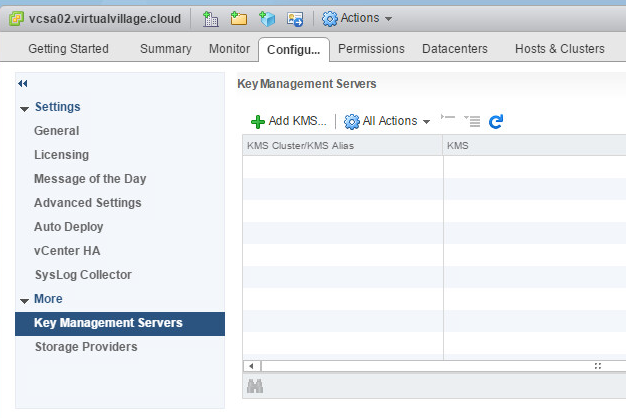
Lets see how to add in our vCenter KMS configuration – it is straight forward You just need to find new tab at web client and add new connection :
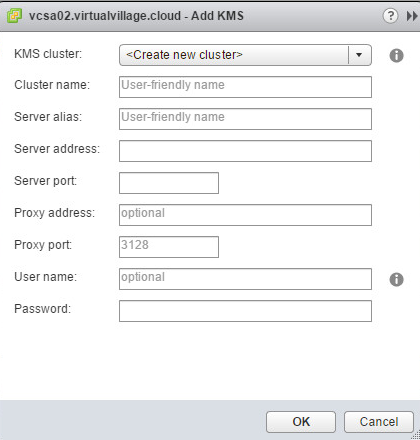
… and finally examples of supported KMS servers (below is not a full list)
Note !!!
most KMIP 1.1 compliant key managers get the approval – but as usual verify with VMware interoperability matrix to have 100% sure
